What are "the seven properties of highly secured devices"?
Revisiting Microsoft's IOT hardening recommendations.

A few years ago, Microsoft's research group released a document (MSR-TR-2020-41 – direct link here) which outlines their opinion on proper security practices of IoT devices.
The material is a bit dated but still absolutely relevant. It's about 15 pages long, so definitely worth a read if you're curious. Here's the short-short version:
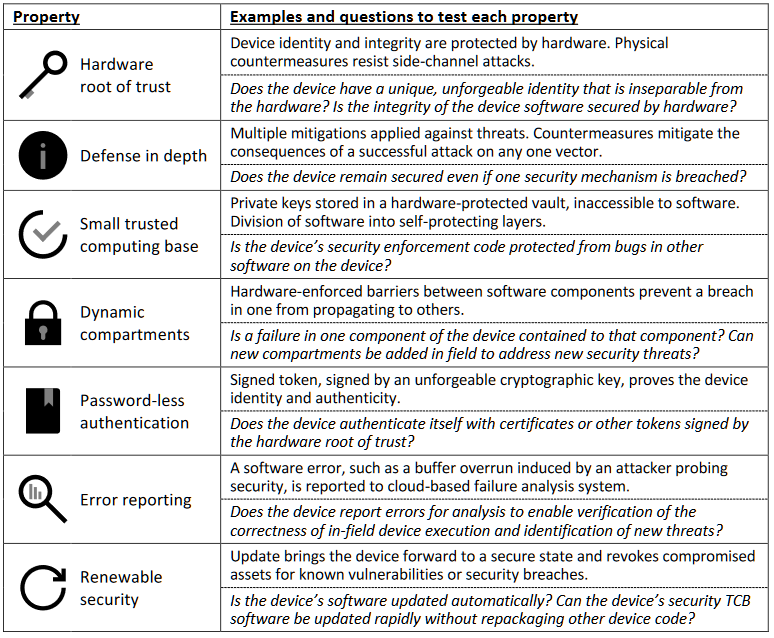
- "Highly secured devices have a hardware root of trust."
- "Highly secured devices have defense in depth."
- "Highly secured devices have a small trusted computing base."
- "Highly secured devices provide dynamic compartments."
- "Highly secured devices use password-less authentication."
- "Highly secured devices have online error reporting."
- "Highly secured devices have renewable security."
There's also a nifty nifty table in the middle of the doc which includes some reflective questions to ask during design processes (all credit to Microsoft for the content):